In many business systems, the Facebook Developer Account is often underestimated, yet it represents one of the highest-risk components. Once a developer account is disabled, the impact goes far beyond a single app—it can disrupt App IDs, API access, ad delivery, login systems, and data reporting across the entire ecosystem.
Many teams are confused by this situation: no ads were running, no obvious policy violations occurred, yet the developer account was still disabled.
To address this issue properly, it is critical to understand one key point: Facebook’s risk control logic for developer accounts is fundamentally different from that applied to ad accounts or personal accounts.
I. Identify the Type of Developer Account Restriction You Are Facing
Under Meta’s 2026 risk control system, developer account restrictions generally fall into three levels. Each level has a significantly different recovery probability.
- Temporary Restriction
This typically involves partial API access suspension. The app still exists, but core APIs such as Login, Marketing API, or Conversions API cannot be used. These cases are usually triggered by abnormal behavior patterns rather than confirmed policy violations. - Developer Account Disabled
This is the most common and impactful scenario. The developer account is flagged for policy violations, and all associated apps become unavailable. Recovery requires a formal review request. - Permanent Ban
This usually follows explicit policy violations or multiple historical offenses. Such bans are nearly irreversible, with an extremely low appeal success rate.
Meta has clearly stated that developer account enforcement decisions are often the result of automated detection combined with manual review, rather than a single trigger.
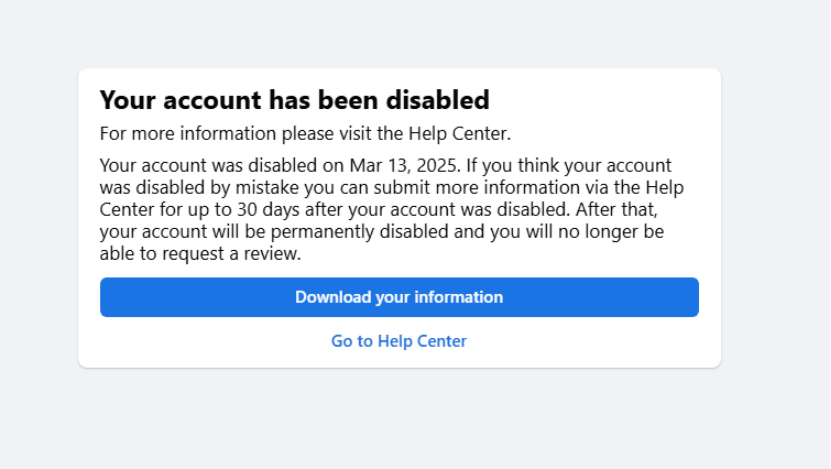
II. Core Reasons Facebook Developer Accounts Are Disabled in 2026
Based on a large number of real-world cases from 2025–2026, the primary causes have shifted away from code-level issues toward behavioral and environment-related risks.
- Mismatch Between Declared App Purpose and Actual Behavior
For example, an app declared as a “login tool” or “analytics tool” may exhibit API usage frequency or data access patterns that clearly exceed the stated purpose. This inconsistency is highly likely to trigger automated audits. - Abnormal API Usage Patterns
This includes sudden spikes in request volume, non-standard usage flows, or multiple apps sharing highly similar calling behavior. Within Meta’s systems, these patterns are often associated with automation or abuse risks. - Risk Propagation From Associated Accounts
Developer accounts are strongly linked to personal Facebook accounts, Business Managers, ad accounts, server IPs, and login devices. Once any linked entity is classified as high risk, the developer account can be affected through association. - Abnormal Login and Operation Environments
Since 2026, Meta has placed significantly higher weight on device fingerprints, IP stability, and login behavior rhythm. Frequent changes in country, IP, or device, or multiple people operating the developer console from shared environments, are considered high-risk signals.
III. Short-Term Solutions After a Developer Account Is Restricted
If your Facebook Developer Account has already been restricted or disabled, the following approaches remain effective and have shown relatively high success rates in real cases.
- Confirm the Restriction Level Before Appealing
The first step is not submitting an appeal immediately, but confirming whether the restriction applies at the app level or the developer account level, and whether the account is marked as eligible for review. Only accounts with a visible “Request Review” option in the Meta Business Help Center have a meaningful chance of recovery. - Focus Appeals on Behavioral Clarification, Not Emotional Explanation
Appeals with higher success rates typically include a clear explanation of the app’s actual use case and business model, a proactive explanation of any abnormal behavior such as testing, migration, or configuration errors, and a description of corrective actions already taken. Generic statements about policy compliance are far less effective than point-by-point responses to risk signals. - Pause All Related Operations During the Review Process
While an appeal is under review, avoid creating new apps, adding developers, or frequently logging into the console. Any abnormal activity during this period may be interpreted as an attempt to bypass risk controls, potentially leading to permanent enforcement.
IV. How to Reduce the Risk of Future Facebook Developer Account Bans
- Treat the Developer Account as a Core Asset
A developer account should not be used as a temporary testing account or shared among multiple users. Its purpose, associated app types, and permission structures should remain stable over time. Frequent repositioning or large permission changes can cause the system to classify the account as high risk.
The developer account should no longer serve as a casual testing tool, should not be mixed with personal daily-use Facebook accounts, and should avoid frequent developer additions or permission restructuring.
- Keep App Behavior Consistent With the Declared Purpose
Actual API usage should remain aligned with the originally declared app purpose. Calling frequency, usage patterns, and data types should avoid sharp fluctuations. Testing and debugging activities should be conducted in isolated environments rather than directly on production apps. - Control Associations Between Accounts
Facebook evaluates relationships between accounts, devices, proxies, and behavior patterns when making risk decisions. Avoid frequent logins from multiple regions or networks, avoid sharing environments with high-risk ad accounts or previously restricted accounts, and minimize frequent changes in country, proxy, or device fingerprints when accessing the developer console. - Maintain a Stable and Independent Network Environment
Frequent changes in country or proxy, or multiple users accessing the developer console from different networks, are treated as instability signals. In practice, IPFoxy’s independent real network proxy is often used to provide a fixed, low-association network environment for developer accounts, reducing the risk of triggering risk controls due to environmental volatility.
IPFoxy is not used to bypass rules, but to provide long-term stable and real independent proxy connections, reduce abnormal login signals caused by IP fluctuations or shared networks, and lower hidden association risks with other accounts or teams.
- Reduce System Misjudgment Caused by High-Frequency Configuration Changes
Operations such as adding members, adjusting permissions, or upgrading app architecture should be performed in stages rather than in rapid succession. From the system’s perspective, accounts with long-term stability and slow, predictable change rhythms are more likely to be classified as trustworthy.
Conclusion
In the 2026 Facebook ecosystem, developer account bans are often the result of long-term risk accumulation rather than a single incident. In the short term, appeals and clarifications can resolve immediate issues. In the long run, only when account structure, behavioral patterns, and operating environments remain consistent and controllable can risk truly be reduced.